Verifiable credentials (VCs)
Verifiable credentials (VCs) are a foundational element of the Self-Sovereign Identity (SSI) ecosystem. They are digital, machine-readable documents that contain a set of claims made by an issuer, which are cryptographically verifiable to ensure their authenticity and integrity.
What are verifiable credentials?
Verifiable credentials (VCs) are digital assertions made by an issuer about a subject, such as a person, organization, or device. These credentials are:
-
Tamper-evident
Designed to show any alterations or tampering, ensuring the data remains trustworthy.
-
Cryptographically verifiable
Uses cryptographic proofs to verify the origin and integrity of the credential.
According to the W3C Verifiable Credentials Data Model:
A credential is a set of one or more claims made by the same entity. Credentials might also include an identifier and metadata to describe properties of the credential, such as the issuer, the validity date and time period, a representative image, verification material, status information, and so on. A verifiable credential is a set of tamper-evident claims and metadata that cryptographically prove who issued it.
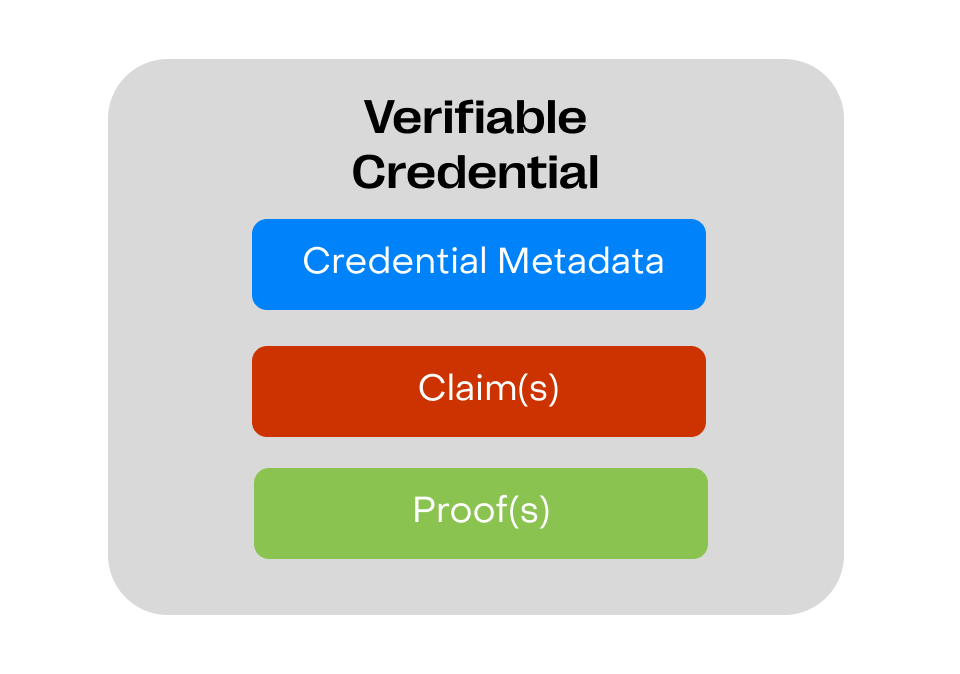
Key components of a verifiable credential
A typical verifiable credentials includes the following components:
- Claims - statements about a subject (for example, name, age, qualification) that the issuer asserts to be true.
- Issuer information - details about the entity that issued the credential, including its decentralized identifier (DID).
- Proof - cryptographic proofs, such as digital signatures, that verify the authenticity and integrity of the credential.
- Schema reference - a link or identifier that points to a public, machine-readable definition of the credential's claims. This ensures the structure, data types, and rules are consistently understood by all parties.
- Metadata - additional data like expiration date, terms of use, and revocation status.
Below is a simple representation of a verifiable credential structure:
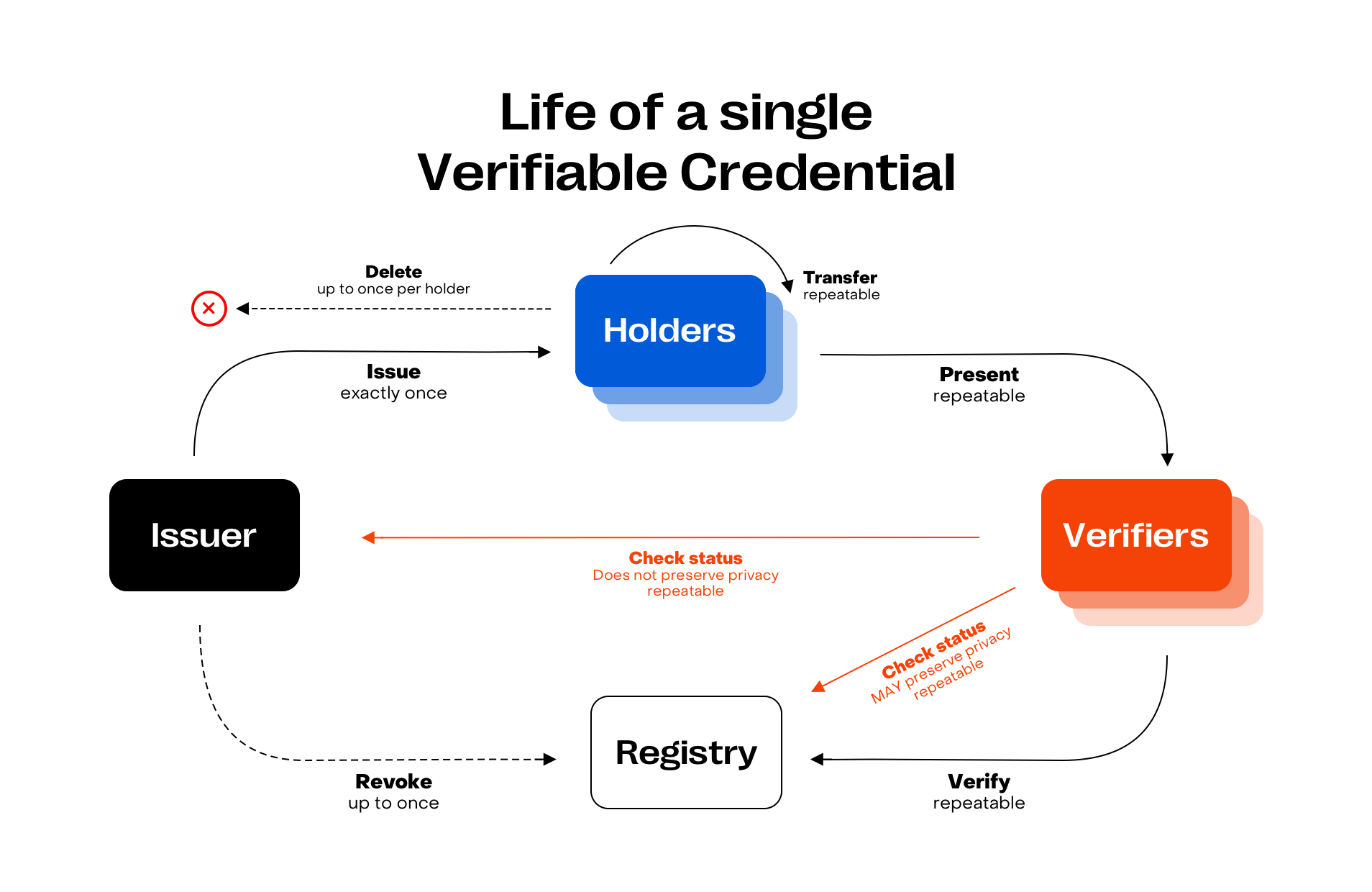
Verifiable credential lifecycle overview
The lifecycle of a verifiable credential involves several key stages:
-
Issuance: The issuer creates a credential containing specific claims and provides it to the holder, who manages and controls it in their Digital wallet.
-
Presentation: The holder presents their credential to a verifier, such as an employer or service provider, who needs to validate the claims.
-
Verification: The verifier checks the authenticity and integrity of the credential and its claims using cryptographic proofs and the issuer's public key.
-
Revocation: The issuer may revoke the credential if it becomes invalid (for example, a revoked license or expired certificate).
-
Expiry: The system treats the credential as invalid after it reaches its expiration date and blocks its verification.
The following image visually represents the verifiable credential lifecycle:
Benefits of verifiable credentials
-
Increased trust
Provides cryptographic proof of the credential's authenticity, reducing fraud and ensuring trust between parties.
-
Enhanced privacy
Enables selective disclosure by sharing only necessary claims and protecting user privacy.
-
Interoperability
Supports multiple digital identity systems and protocols, enabling seamless interactions across different platforms.
-
Efficiency
Streamlines verification processes by eliminating the need for paper-based documents and manual checks.
Further reading
- Dive deeper into the concept of verifiable credentials and their role in decentralized identity models.
- Explore how digital wallets store and manage verifiable credentials.